Kerberos 是一种身份认证协议被广泛运用在大数据生态中甚至可以说是大数据身份认证的事实标准本文将详细说明 Kerberos 原理PS. Kerberos mythology or Cerberus the hound of Hades.

Flink Configuring Kerberos Authentication Huawei Enterprise Support Community Unified Communications Public Security Ip Telephony
Le protocole Kerberos est issu du projet Athena du MIT mené par Miller et Neuman.
Kerberos. It is designed to provide strong authentication for clientserver applications by using secret-key cryptography. Kerberos authentication supports a delegation mechanism that enables a service to act on behalf of its client when connecting to other services. Deploy your own video surveillance system in a few minutes anywhere you want using Raspberry Pi Docker or Balena Cloud.
The main components of Kerberos are. Kerberos Dante a character from Saint Seiya. If a non-authorized user has access to the Key Distribution Center.
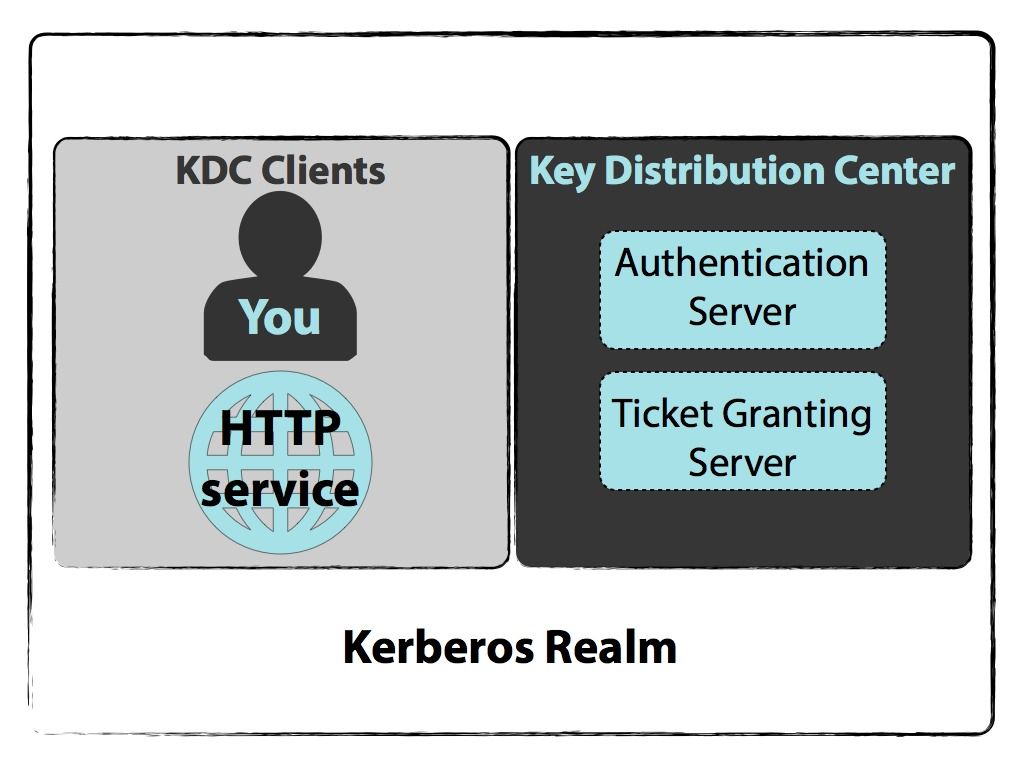
Each user and service on the network is a principal. It uses secret-key cryptography and a trusted third party for authenticating client. Kerberos runs as a third-party trusted server known as the Key Distribution Center KDC.
Clients obtain tickets from the Kerberos Key Distribution Center KDC and they present these tickets to servers when connections are established. Kerberos is a computer network security protocol that authenticates service requests between two or more trusted hosts across an untrusted network like the internet. With SSO you prove your identity once to Kerberos and then Kerberos passes your TGT to other services or machines as proof of your identity.
Kerberos protocol a computer network authentication protocol to allow server communication over a non-secure network. Kerberos is available in many commercial products as well. The weakest link in the Kerberos chain is the password.
A free implementation of this protocol is available from the Massachusetts Institute of Technology. The core product backbone of the entire Kerberosio ecosystem completely free and open source. Kerberos may refer to.
Kerberos is a network authentication protocol. Kerberos is adopted by a huge number of industries so any new weaknesses in its security protocol or in underlying modules are quickly corrected. It is designed at MIT to allow network resources in a secure manner.
Kerberos moon a moon of Pluto. The weaknesses of Kerberos are.
Given this stature it has become one of the protocols most targeted for abuse by adversaries of all shades. Kerberos excels at Single-Sign-On SSO which makes it much more usable in a modern internet based and connected workplace. Kerberos is a well-known and widely used authentication protocol that also lies at the heart of Microsofts Active Directory.
It is designed at MIT to allow network resources in a secure manner. La version 5 du protocole Kerberos a été normalisée par lIETF dans les RFC 1510 septembre 1993 et. Kerberos is a computer network authentication protocol.
In this article we will see discussed the Kerberos concept. Using Kerberos authentication within a domain or in a forest allows the user or service access to resources permitted by administrators without multiple requests for credentials. Kerberos Productions a game development studio.
Krematorium Kerberos od svého počátku mělo cíl poskytovat kremační služby důstojným a příjemným způsobem. Kerberos tickets represent the clients network credentials. Klademe důraz na trpělivou komunikaci s majiteli zemřelých zvířat protože si uvědomujeme bolest kterou každý prožívá když mu jeho mazlíček umře.
The Authentication Server performs the initial authentication and ticket for Ticket Granting Service. The Kerberos protocol defines how clients interact with a network authentication service. Transparent video surveillance for everybody everywhere.

Explain Like I M 5 Kerberos Lynn Root Explained Words Cryptography

Soul Sacrifice Kerberos Fantasy Creatures Character Art Cool Monsters

Selecthiveql Nifi Connection Hives

Kerberos Saga Armor Concept Dieselpunk Retro Futuristic

Cerberus Or Kerberos In Greek And Roman Mythology Is A Multi Headed Usually Three Headed Dog Or Hel Greek And Roman Mythology Greek Mythology Greek Myths

Kerberos Explained Security Companies Band Patches Microsoft

Request Based Versus Session Based Kerberos Authentication Or The Authpersistnonntlm Parameter Request Sharepoint Base

Part2 Step By Step Guide For Configuring Kerberos Authentication In Sharepoint 2013 2016 Sharepoint Microsoft Dynamics Step Guide

How Do I Use Ntlm Or Kerberos Authentication To Access A Cifs Share In 2021 Trust In Relationships Messages Access

Cracking Kerberos Tgs Tickets Using Kerberoast Exploiting Kerberos To Compromise The Active Directory Domain Active Directory Innovation Technology Domain

Kerbrute A Tool To Perform Kerberos Pre Auth Bruteforcing Cyber Security 20 Years Old Linux

Freeletics Workout Kerberos Das Workout Geht Uber 3 Runden Mit Jeweils 3 Ubungen Pro Runde Freeletics Freeletics Ubungen Freeletics Workout

Kerberos Architecture Computer Help Windows Server Microsoft

Kerberos Architecture Computer Help Windows Server Microsoft

What Is Kerberos And How It Works Social Media Infographic Computer Network Infographic



